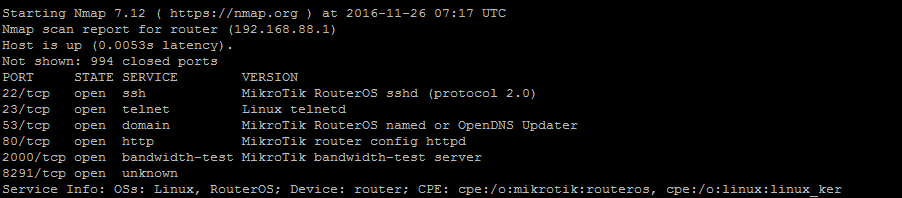
Determining whether a compromised computer is a VM (Virtual Machine) or not is important when orienting yourself in a network. If a breached computer is a VM that means that there’s a hypervisor on the network that could be a valuable target.
If a compromised computer is residing on a hypervisor there is also a chance that you’re now on a honeypot system and being observed, which is not good from a pentester’s perspective. Typically we wouldn't expect to find a Windows XP, Vista, 7, or 10 computers on a hypervisor but if you do that is somewhat suspicious, which makes this all the more important.
The checkvm command will determine whether or not a host is a VM or not, and what kind of hypervisor it’s running on:
run checkvm
The command output should indicate whether you're on a virtual computer or not, and what type of hypervisor it's running on if it is virtualized.