Finding Windows Versions with Metasploit
Need help with implementation or an upcoming project? We offer professional services at reasonable rates to help you with your next network rollout, security audit, architecture design, and more. Click here to find out more.
If you've gained access to a Windows domain, how would you go about determining the types of Windows computers on the rest of the network? You could run a port scan with Nmap or the Metasploit db_nmap command, but port scans garner a lot of attention. Instead we can take advantage of a very common Windows service - SMB. Server Message Block (SMB) operates on TCP:445, and runs on all modern versions of Windows, including Windows Server.
It allows computers to share files and printers, and Linux / UNIX platforms can run a compatible service called SAMBA. Fortunately for us it also tells a lot about the system that's running it.
We'll use the auxiliary/scanner/smb/smb_version module to probe hosts we've discovered so far for their SMB versions, which are listed below:
- v1.0 Windows XP, Server 2003 (Deprecated)
- v2.0: Windows Vista
- v2.1: Windows 7, Server 2008 R2
- v3.0: Windows 8, Server 2012
- v3.0.2: Windows 8.1, Server 2012 R2
- v3.1.1: Windows 10, Server 2016
We can get the SMB version without authenticating to the remote computer, SMB traffic on a local network isn't unusual at all, and we only need to probe one port to get what we need.
use auxiliary/scanner/smb/smb_version
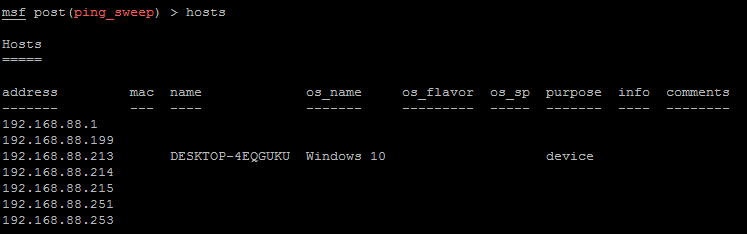
I already have a few hosts listed when we run the hosts command, found by running a ping sweep, but I don't have much information on them except for the host I have a Meterpreter shell on:
Unknown hosts
I'll use the hosts -R command to take all the IPs listed under hosts and set them as RHOSTS:
hosts -R
We don't need to set any other options, though if we had valid domain credentials we could set the SMBUser, SMBPass, and SMBDomain options.
Run the SMB version scanner:
run
The scan only takes a few moments, and we can lists our hosts again:
Discovered Windows 10 computers
The SMB version scan found the only other Windows machine on this network - a Windows 10 Pro computer. We can further target our exploits and social engineering activities with the new information.